
Technology is an integral part of our daily lives. Most businesses have heavily utilized it for a range of purposes, and everything has become more efficient and fast-paced. It is unfortunate, however, that some corrupt people take advantage of technological advancements and create malware in order to obtain illegal money. This is where Software vulnerabilities come in
An electronic device functions with software composed of programs, procedures, and routines. Due to the synthetic nature of software programs, it is usual to experience some errors and glitches during their development causing software vulnerabilities.

The goal of this article is to provide you with an explanation of what software vulnerabilities are and what causes them. Next, we will discuss some of the most common software vulnerabilities and how to prevent them from occurring.
At the end of this article, we will discuss some of the most important factors to consider when choosing a quality software development company.
Software vulnerabilities refers to weaknesses or flaws in software code that are usually attributed to glitches, flaws, or deficiencies.
An attacker can exploit or manipulate software vulnerabilities to damage your software system. The failure to address it can cause harm to your software and result in financial losses, particularly if hackers manipulate your data to steal money from you.
A hacker's most common objective is to ruin the reputation of the company that they hack. The problem of software vulnerabilities is widespread throughout the world, but it can be prevented if your software is constantly tested and developed.
A variety of factors can cause software vulnerabilities. For instance, insecure coding practices could result in vulnerable code due to certain behaviors, policies, or habits. It could be caused by developers under pressure to complete a specific task on time, which compromises security.
There is also the possibility that the developers may unknowingly use an algorithm that has become obsolete due to a threat landscape, such as a broken algorithm that is no longer suitable. A software vulnerability could also result from reusing vulnerable codes that have not been evaluated for security. In order to minimize the risk of this type of risk, it is important to learn more about these possible causes.
Cybersecurity incidents are often caused by insufficient logging and monitoring. This vulnerability occurs as a result of a failure to properly log off critical security flaws and the inability to monitor the system consistently. As a result, malicious activities are more difficult to detect, and the incident handling process is negatively affected.
Therefore ensure that your server logs are backed up and synced to another server to prevent a cyber attacker from wiping out all data after hacking your server. The system should also be reviewed and ensure that logins, passwords, crucial transactions, and other sensitive activities are logged. Administrators should be notified if specific issues have arisen in order to take immediate action.
Sensitive data exposure is also considered a software vulnerability and is one of the most common types of security breaches. In the event that sensitive information, such as credentials, credit card details, social security numbers, and other personal information, is compromised, those details become vulnerable to theft or cyber-attacks.
In order to prevent this threat, good security hygiene should be implemented, such as classifying, storing, and transmitting data, identifying sensitive data as per privacy laws, and enforcing proper authentication.
A critical breach may be caused by the use of components with unknown vulnerabilities. Whatever vulnerability the element possesses will be reflected in your code. You will also experience issues with rogue libraries since they exploit your code in order to steal highly valuable data. You can never guarantee that your components will be 100% secure since all complex software contains vulnerabilities.
Make sure you are familiar with what components you are using and what version of each. Provide a method for seamlessly downloading, testing, and releasing patches when vulnerabilities are discovered.
The most important thing is to have policies on how open source and third-party integrations are used. The code that your company does not write must go through an extensive screening process. For the purpose of increasing trust and confidence in users, it is advisable to utilize third-party software with a Code Signing Certificate.
A great deal of diligence is put into finding any opening or vulnerability by attackers. It is unlikely that they will not take advantage of the opportunity to gain access to any sensitive information. Poorly designed and poorly implemented accessibility controls can lead to the extraction and compromise of sensitive information. Therefore, ensuring the client's safety while using the software begins with properly managing sessions and data authentication.
There are several adverse effects that can result from software security weaknesses. As a result, you should take all the necessary safety precautions while developing the software in order to avoid these problems. Different methods for automatically detecting weaknesses in a software application are important for software developers.
The traversal of directories is common. Hackers can access and read files on the server, especially if the server is running. Files such as code and data, authentication credentials for back-end systems, and operating system files may be included. Possible solutions:
Input filtering is another well-known problem. An untrusted input may result in an unvalidated redirect or forward when the application accepts untrusted input, possibly rerouting the request to the input's URL.
The first option would be to avoid redirects altogether since they're rarely needed. Ensure input is clean by creating a static list of trusted URLs, and confirm that all redirects go through a page that explains they're leaving your site.
A cross-site scripting flaw can allow malicious agents to execute their own scripts within targeted software. An application may contain cross-site scripting vulnerabilities when it includes untrusted files in a new web page without performing any real validation. Also, the problem can occur when a website is updated with user-supplied data using a browser API capable of producing HTML or JavaScript. This leads to the development of these software vulnerabilities.
Sanitizing input can prevent an XSS vulnerability from being exploited. It will help to prevent user input from being used to manipulate software vulnerabilities and inject them into websites. It will also be helpful to protect against malicious injection by validating and escaping user input.
Testing your software often is a good practice, as it will help you identify and eliminate vulnerabilities as quickly as possible. A variety of testing techniques can be used to test your software, including code analysis tools, white box testing, and black box testing.
Make sure secure coding principles are defined and enforced. The use of secure coding standards should be included in this process. Furthermore, it will assist you in writing, testing, inspecting, analyzing, and demonstrating your code effectively.
Look out for vulnerabilities in your system proactively to limit an attacker's window of opportunity. Check regularly for new risks by reviewing, analyzing, and testing software. This will ensure that flaws are identified and reported as soon as possible, thereby ensuring an efficient response scheme.
Digitally signing your code will make it tamper-proof, making it impossible for anyone to manipulate your code. Using a code signing certificate will allow you to create secure files and prevent hackers from inserting security vulnerabilities into your code as a result.
One of the things that will contribute to the success of your business is choosing a quality software development vendor. Choosing the right custom software development company is essential to your custom software's quality, value, and success. You should be able to find a company that fits your needs and has the expertise and experience you need to develop your unique project.
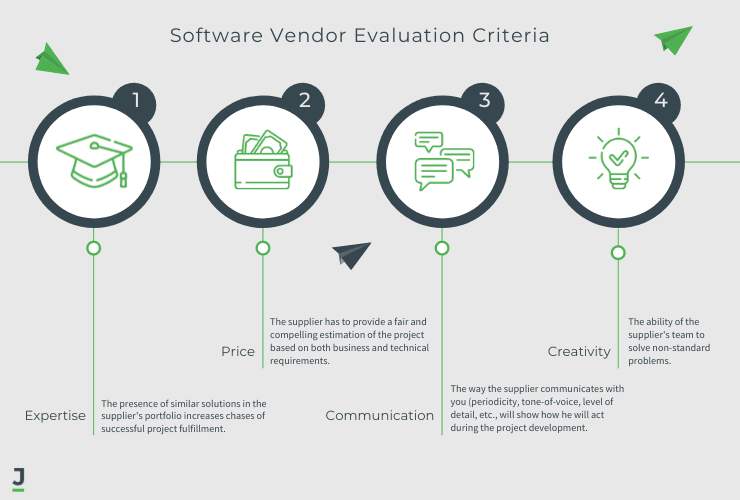
Make sure to conduct thorough research before hiring a software development company, but there are several other factors you should consider as well:
Reviewing a company's portfolio before approaching them is always a good idea. As a first step, this allows you to check how experienced the company is by analyzing the experience of its past clients. A company's experience in software development will be demonstrated by the number of projects they showcase. It suggests a high degree of stability and experience. On the other hand, a newly established company with only a small number of projects in its portfolio may not possess sufficient experience to address new issues as quickly as they arise.
If you take a look at the company's portfolio, you will be able to determine what sort of clients they work with. Which technologies have they used, and what types of projects have they completed in the past?
A vendor's ability to adjust the number of developers on a project's team is important to consider. It will not only assist you in adjusting your costs but also help you in determining whether the vendor is flexible enough to meet your business's needs.
Having a good reputation and being preferred and referred to by many companies is one of the main indicators of a good software development vendor. You should hire a software development company that has experience in developing software or a system similar to what you want to develop. Furthermore, you should research whether this company has previously dealt with or worked with remote teams.
Make sure you thoroughly evaluate your options in order to choose the most cost-effective option, not just the cheapest one. When choosing a vendor, you should consider the cost-effectiveness of the software development services you will procure. Knowing what kind of business development you require will help you determine the size of your budget when it comes time for you to hire their services. A low price does not necessarily indicate a high-quality product. Outsourcing also influences the price.
You may wish to inquire about the platform and technologies the software development company uses, as well as the characteristics of each platform, in order to determine which one you would like to use for your custom software. During the development of software, testing is an important factor to take into account. This is because it allows developers to identify software vulnerabilities and repair them as quickly as possible.
Checking a vendor's history is the best way to determine if they are secure against cyberattacks. Has there ever been a data breach or hacking incident? Keep in mind that anyone can get hacked. There has even been a breach of Microsoft's security by 2020 malware.
In order to evaluate a company's response to such problems, you need to examine how it has handled them. A good software development vendor learns from its vulnerabilities and strengthens its security as a result of the attack. It is important to note that Microsoft may have been a victim of the attack, but they were also instrumental in dismantling the malware months after the attack.
A vendor who is repeatedly subjected to cyberattacks should be avoided. This indicates that they do not attempt to innovate and upgrade their security in order to prevent future attacks.
When it comes to a great software development company, the process doesn't end when the software is sold and used. Regardless of how rigorous the testing process is, your software is going to have bugs and errors that end-users will encounter when using it. Reputable vendors continually release patches and updates in order to try to fix bugs and add new features to their products.
The security of the internet is also constantly changing. There is a continuing evolution in the methods used by hackers, and software development vendors must be prepared for this. There is a possibility that software that is considered secure today will not be secure in the future.
The presence of accompanying code-signing certificates is another sign of a legitimate and effective software developer. A code-signing certificate indicates that the software offered by your software developer is authentic and does not contain any malicious code. The certificates also provide protection against various types of malware, such as viruses and spyware, on the software code and files.
Data breaches and hacks can result in millions of dollars in losses for companies and organizations. The good news is that you can still win the battle against malware and viruses by selecting software development companies that have rigorous testing phases, not only prior to launch but also on a continual basis, to ensure that their security is superior to their competitors.
The best software development partner does more than meet your organization's needs. Ensure that you do the necessary research before selecting a software development vendor for your company. Finding the right vendor for your business can rest assured that your company is protected from all looming threats.
Even though finding a company of this type is challenging, the tips in the article will help you begin your search. A leader in software development, PolyUno develops solutions for businesses across the globe. Through a scalable, efficient, and powerful software application development process, we help you build software applications that meet your business needs.